Small Business Cybersecurity Audit
How safe is your business from disruption due to a breach in your computer security? If you’re not sure, Hartland Computer Services will help you identify risks you may have and provide you with actionable recommendations to mitigate those risks. Our Small Business Cybersecurity Audit builds upon our Two-Hour Computer Security Review, providing your business with a starting point for a secure, sustainable IT environment.
Computer-related business risks come in many different forms, “hacking attacks” attract the most attention in the press but most security breaches start from inside the business. Data may be exfiltrated via viruses, spyware, over your WiFi or directly over the internet by determined attackers or opportunists. Data extortion, where an opportunistic attacker encrypts your data and holds it hostage, is becoming an increasingly common occurrence in small businesses in the last 5 years. Some risks are more mundane, fire, flood, physical theft. Our goal is to help you identify where your risks are and to suggest cost-effective ways to reduce them.
A Simple, Deliverables-Based Approach
We have over 25 years experience in Management Consulting and IT in the US and Europe. In that time, we’ve come to develop a notion that, if there’s no document, then no real work was done. So, our Cybersecurity Audit includes a collection of actionable documents that you can use to improve your security and maintain it going forward.
Our initial Cybersecurity Audit includes the following activities:
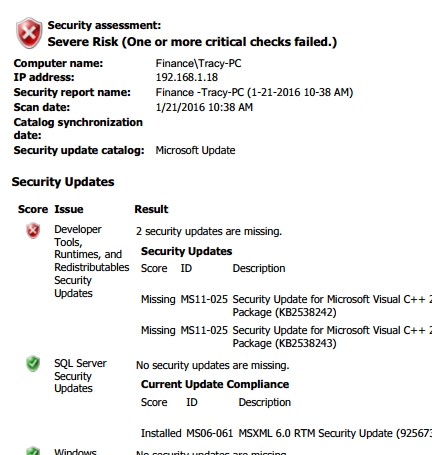
Baseline Security Audit
- Provides Red/Amber/Green status on 14 key security areas within Microsoft Windows along with remedial-steps recommendations (if needed) for each individual computer.
Hardware/Software Audit
- Extensive documentation on each workstation’s hardware and software configuration in Microsoft Word format so it can be updated and managed.
Antivirus Security Review
- Identify and provide feedback on virus and spyware protection provided by current antivirus solution(s).
Network Security Review
- Identify areas of weakness or potential improvement in security of current wired and wireless networks
- Includes analysis and recommendations for WiFi, backups, firewalls, routers, etc.
Security Vulnerability Remediation
It’s our hope that you are sufficiently pleased with the quality of our work and professionalism that, should you require assistance with shoring-up any security deficiencies, you will choose us to help you with that work. But regardless of the outcome, or future requirements, our Cybersecurity Audit will give you the peace of mind that you’re in control of your business, your business data and your IT infrastructure.
