Computer Security Review for Small Business
Hardly a week goes by without a major computer network security breach making news headlines. If major corporations, health care providers and governments agencies can’t keep their data safe, what chance do we small-to-medium businesses have? Well, a pretty good chance actually.
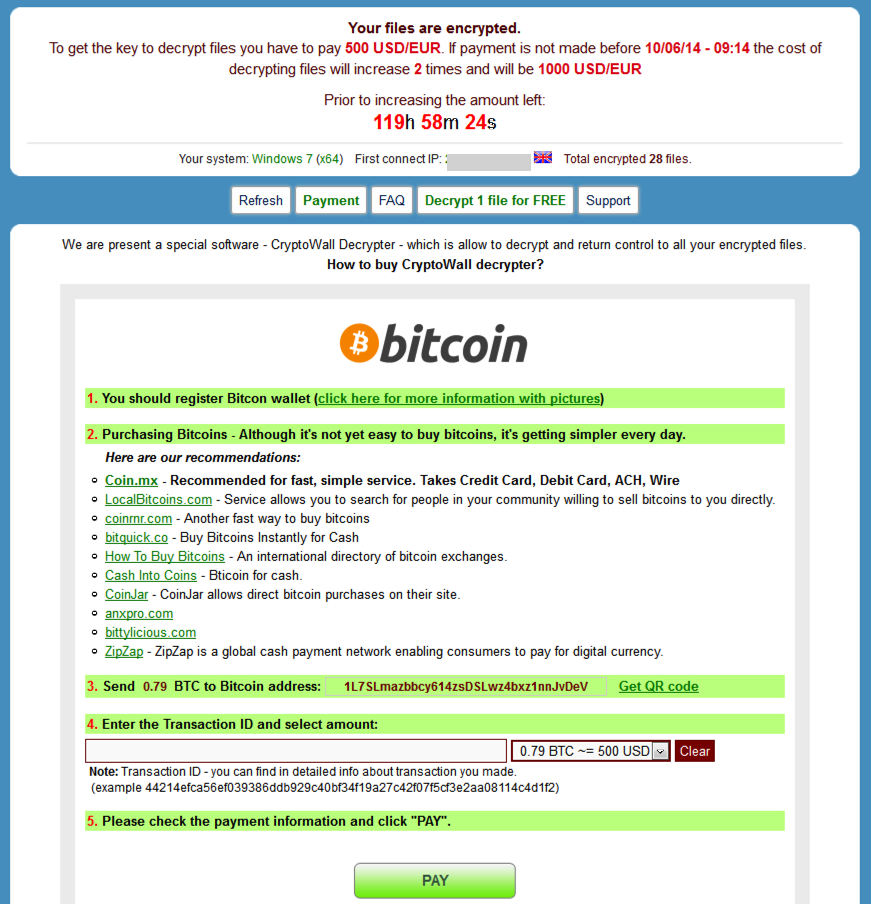
Most Data Breaches Start From the Inside-Out
Contrary to the popular notion of nerdy “hackers” breaking into your systems from somewhere on the internet, most data loss and downtime events are a result of a bad-actor program or routine inside your network. Someone in your organization unintentionally installs a piece of Spyware or a Trojan Horse onto their computer, giving it access to your network, your data and programs. From there, a miscreant can encrypt your data or collect it and send it out over the internet. Even your up-to-date antivirus may be oblivious to this.
In Two-Hours or Less, We’ll Assess Computer Vulnerabilities, Plug Holes, and Suggest Solutions to Systemic Risks We Identify
Windows Security
- Check hard drive operation for early signs of failure,
- Review operation of Windows Update and ensure the all appropriate security updates have been installed,
- Check common security breach vectors for updates.
Spyware Review
- Install and run specialized Spyware detection software, take appropriate action to remove any items found,
- Manual check of browsers for problem plug-ins and add-ons,
- Review installed software for undesirable applications.
Antivirus Review
- Review installation, operation and update status of workstation antivirus solutions.
- Perform second-opinion scan for viruses if needed.
Networking Review
- Check Internet Router security and settings
- Review WiFi security
Who Needs This Kind of Review?
Any business with two or more workstations can benefit from our Security Review. According to one study, 70% of business that suffer a serious data loss are out of business within 2 years. Recovery or re-creation of your customer records, financial data or creative and marketing materials can be extremely time consuming and costly. Miscreants now target small businesses not just to steal their business data but to hold it hostage for ransom. Such events are tremendously disruptive to the operation of SMBs. By reviewing your IT and data security before you are targeted, you can minimize your exposure to such risk.
